Programmers Often Build Trapdoors Into Programs During System Development
Programmers often build trapdoors into programs during system development. Programmers often build trapdoors into programs during system development. Programmers often build trapdoors into programs during system development. Programmers often build trapdoors into programs during system development.
Programmers often build trapdoors into programs during system development True from COMPUTER S 101 at Texas College. TF Programmers often build trapdoors into programs during system development. Programmers often build trapdoors into programs during system development.
Do Programmers often build trapdoors into programs during system development. Expert solutions for 101. The element of bargained-for exchange distinguishes contracts from gifts.
A keygen distributes user names and. Asked Mar 26 2019 in Computer Science Information Technology by vsandschafer. Truefalse Programmers often build trapdoors into programs during system development.
A rootkit can be a back door. Perpetrators of back doors trick their victims into interacting with phony websites. Programmers often build trapdoors into programs during system development.
Users can purchase a software program that selectively blocks cookies like the kind shown in the accompanying figure. Programmers often build trapdoors into programs during system development. Perpetrators of back doors trick their victims into interacting with phony websites.
Any illegal act involving a computer generally is referred to as1277967. Answer the following statement true T or false F information-technology.
Programmers often build trapdoors into programs during system development True from COMPUTER S 101 at Texas College.
Do Programmers often build trapdoors into programs during system development. Cybercrime laws are consistent between states and countries making it easy to reach a consensus as to what is illegal Passwords and passphrases that are more than four characters contain uppercase and lowercase letters numbers and special characters are the most secure PINs are not the same as passwords Programmers often build trapdoors into programs during system development. A rootkit can be a back door. False Personal firewalls constantly monitor all transmissions to and from a computer and may inform a. Secure sites typically use digital certificates along with security protocols. Programmers often build trapdoors into programs during system development. TF Programmers often build trapdoors into programs during system development. Any illegal act involving a computer generally is referred to as1277967. Tools such as a risk assessment form and a risk severity matrix are used to.
Answered Mar 26 2019 by. Programmers often build trapdoors into programs during system development. Erikson called the psychosocial developmental stage that occurs between 3 and 6 years of age _____. Perpetrators of back doors trick their victims into interacting with phony websites. Asked May 10 in Other by gaurav96 -28522 points 0 votes. Programmers often build trapdoors into programs during system development. Programmers often build trapdoors into programs during system development.

















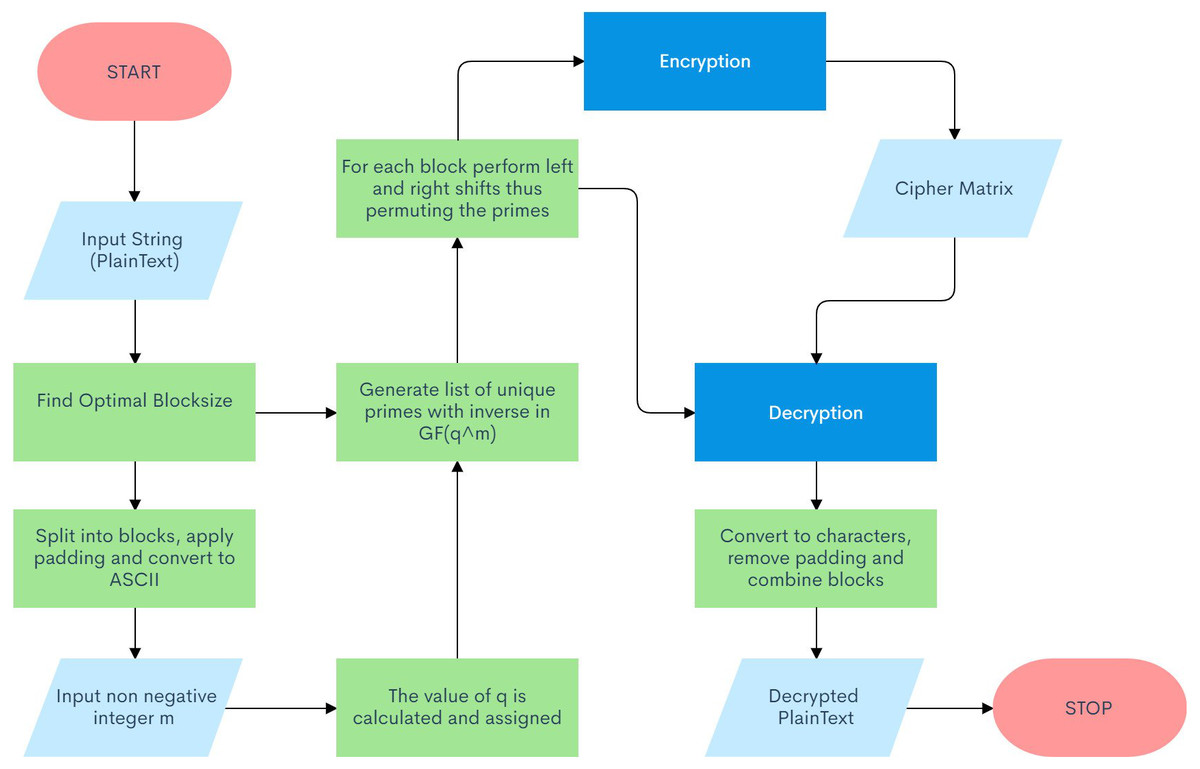

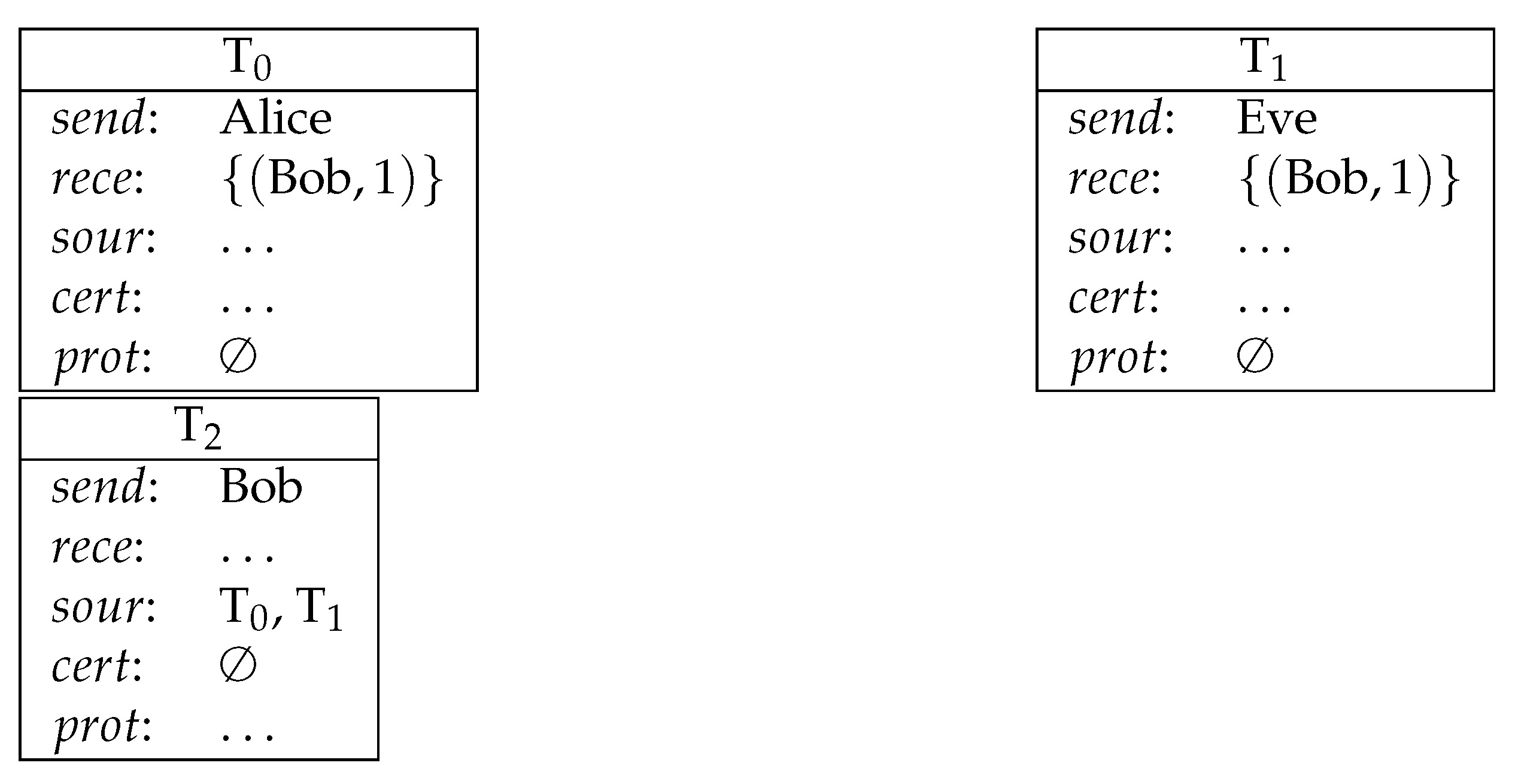
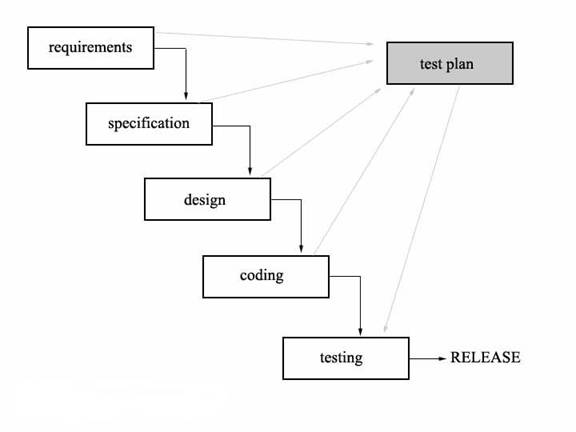






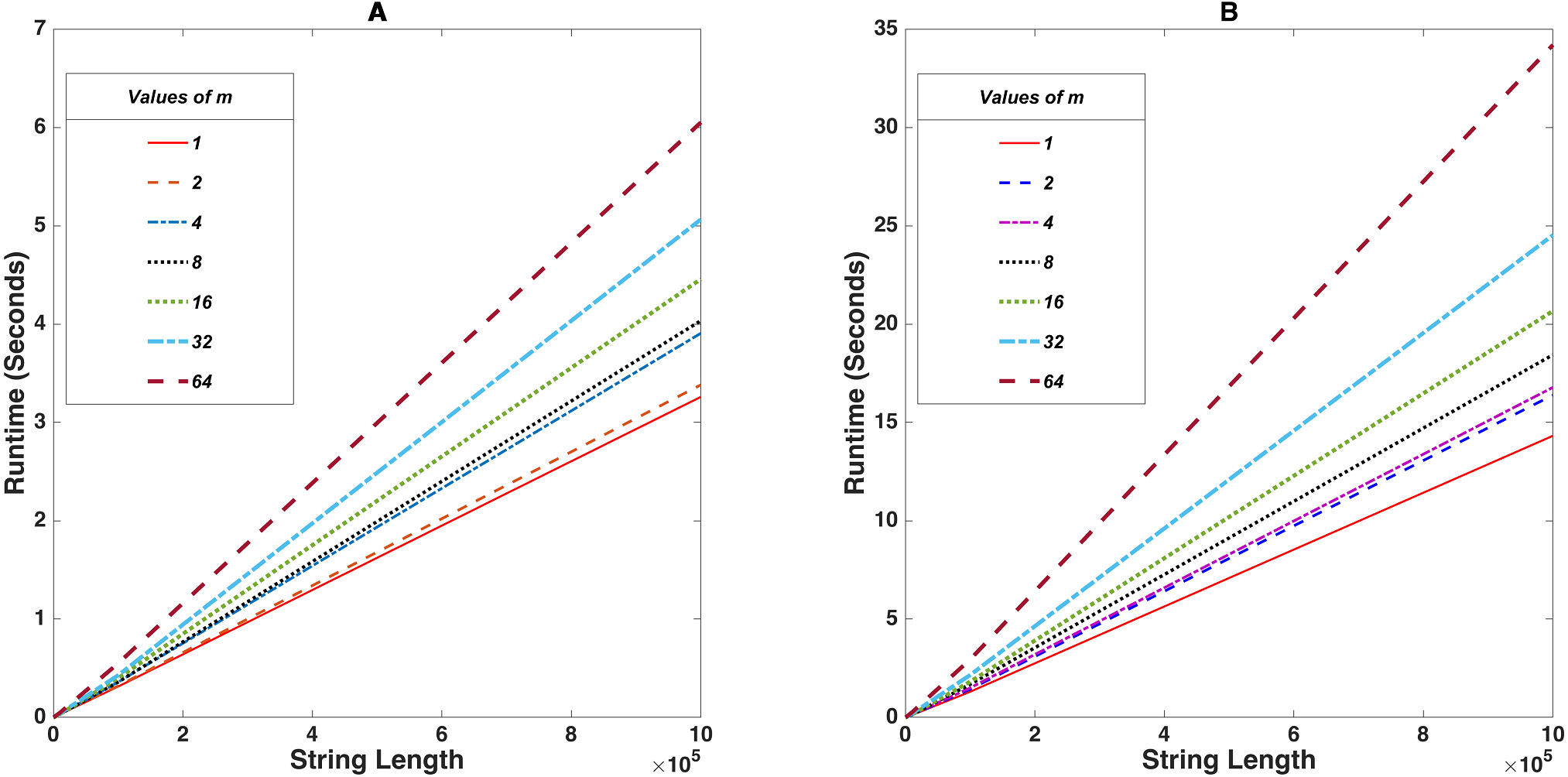




Post a Comment for "Programmers Often Build Trapdoors Into Programs During System Development"